LDAP
In the “Rukovoditel” program there is an integration mechanism with the LDAP, which allows creating new users and assigning them rights automatically.
Let’s have an Active Directory (AD) domain named MyCompany.org. The following scenario for registering a new user in the program is assumed:
- The domain administrator creates domain user groups that are allowed to register in the program and include AD user accounts in this group.
- The domain administrator creates domain user groups that correspond to the groups in the Rukovoditel, and includes a user account in the required domain groups.
- The user first logs into the program using LDAP, the program creates a new user account, fills the user information with data from the AD account, and places the user account in his access group.
- The registration process is completed, the user can fully work in the program
So, you must first configure the settings on the LDAP Configuration page:
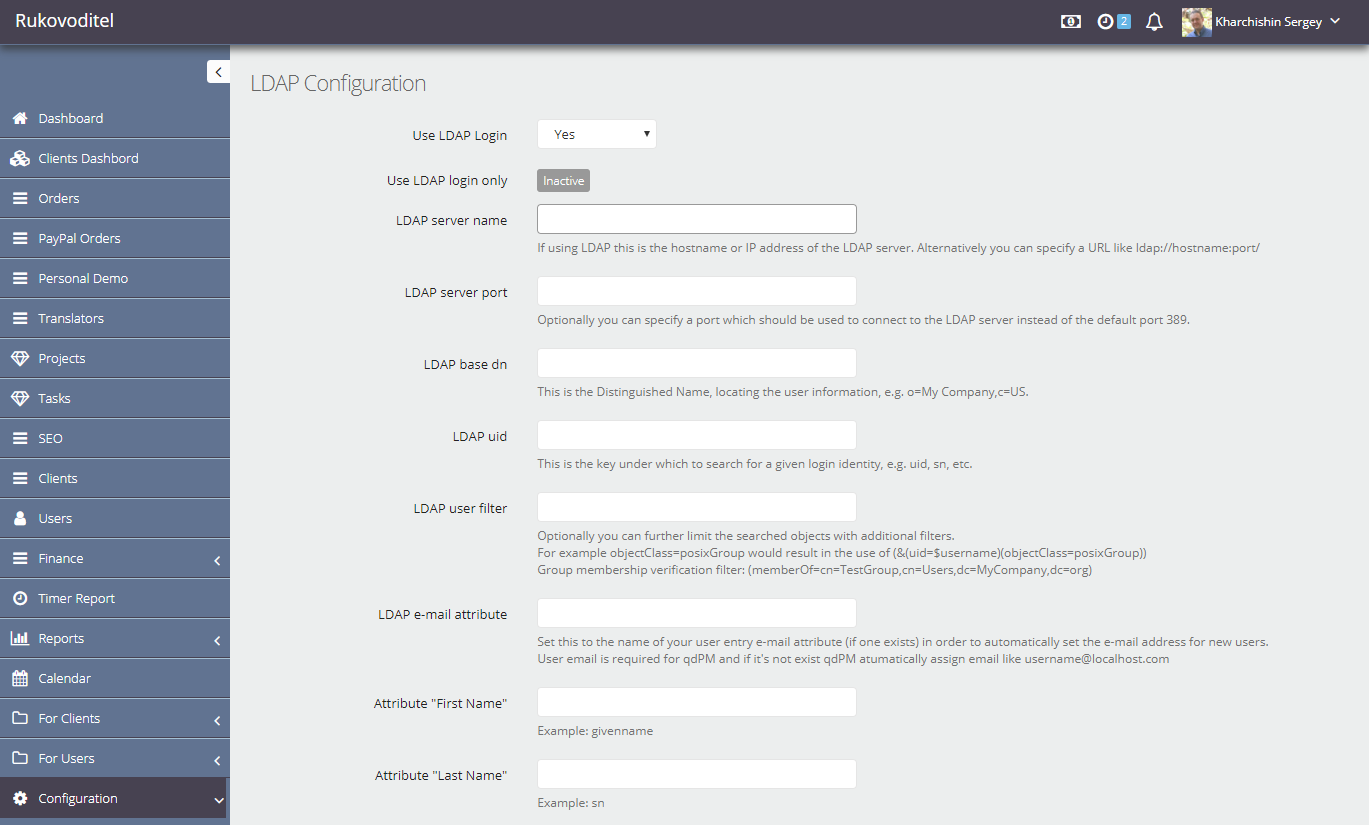
- Use LDAP Login – yes
- Use LDAP login only – this parameter is controlled by the variable CFG_USE_LDAP_LOGIN_ONLY from the server.php file. If this variable is true, only the passwords from the AD accounts can be used to login, otherwise both input options are possible.
- LDAP server name – network name or IP address of the domain controller
- LDAP server port – port on which the LDAP service is running
- LDAP base dn – the point in the LDAP hierarchy from which the search will begin. It is usually enough to set the value to “DC = MyCompany, DC = org”
- LDAP uid – an attribute that contains the unique name of the user account, usually “sAMAccountName”
- LDAP user filter – here you can specify an additional condition that is used when searching for the user. If you do not specify anything – the program will be able to register any user who has an account in the domain. But if you specify a condition of the form:
(memberOf=cn=RukovGroup,cn=Users,dc=MyCompany,dc=org)
then only members of the RukovGroup domain group will be able to register, which is what the scenario requires.
- LDAP e-mail attribute – attribute of the user account AD, in which the mail address is stored, usually “mail”
- Attribute “First Name” – attribute of the account user AD, in which the user name is stored, for example “givenname”
- Attribute “Last Name” – attribute of the user account AD, which stores the user’s last name, for example “sn”
- LDAP user dn, LDAP password – login and password for the user to connect to AD.
After these settings, new users will be able to register in the program, now you need to configure the conditions for joining access groups.
Automatic assignment of access group
On the “Users Access Groups” page for each group on the “LDAP Configuration” tab, fill in the “LDAP filter” field:
|
Access Group in Rukovoditel |
LDAP Filter |
|
Client |
(memberOf=cn=client,cn=Users,dc=MyCompany,dc=org) |
|
Developer |
(memberOf=cn=developer,cn=Users,dc=MyCompany,dc=org) |
|
Manager |
(memberOf=cn=manager,cn=Users,dc=MyCompany,dc=org) |
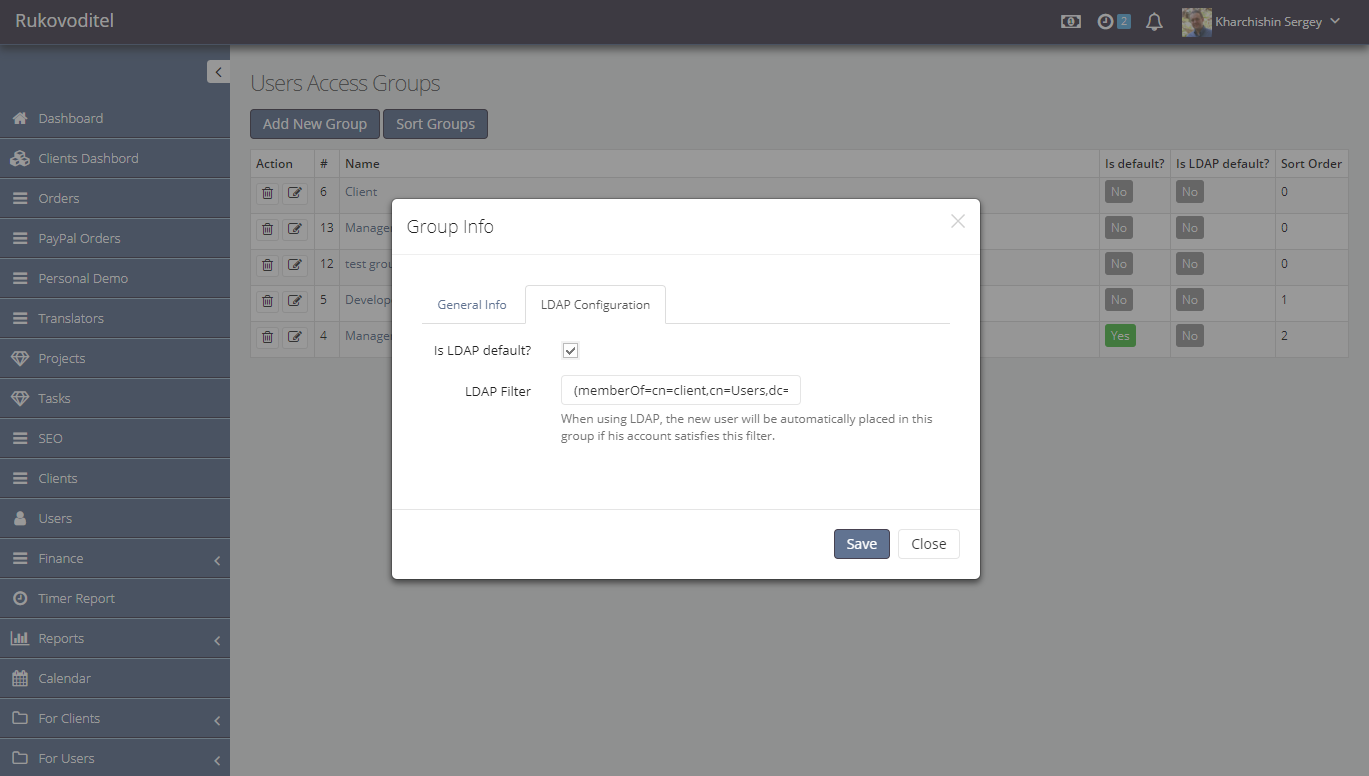
Thus, if the user account is in the domain group “client”, his account in the program will be placed in the group” Client ” and so on.
The filters are checked before the first match. If none of the filters match or are not set, the user account will be placed in the group that has the “is LDAP default” flag.
To view the attributes of accounts in AD, you can use for example a free program Active Directory Explorer.